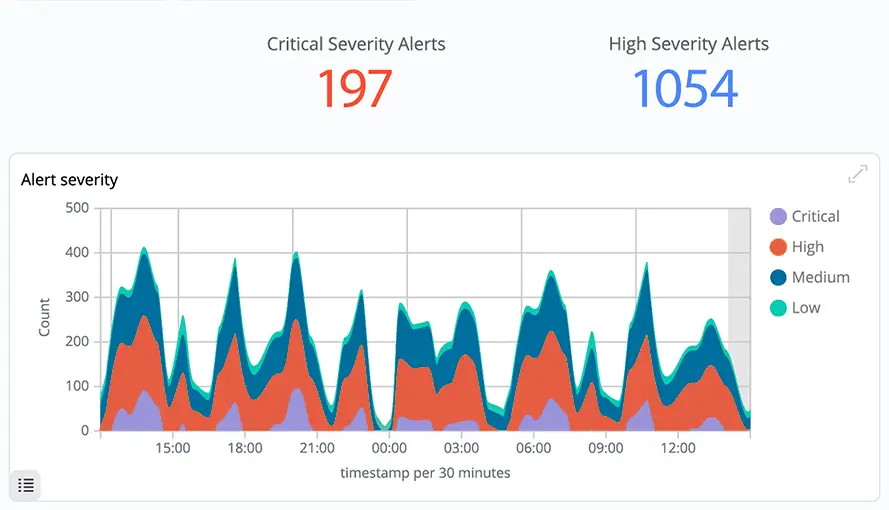
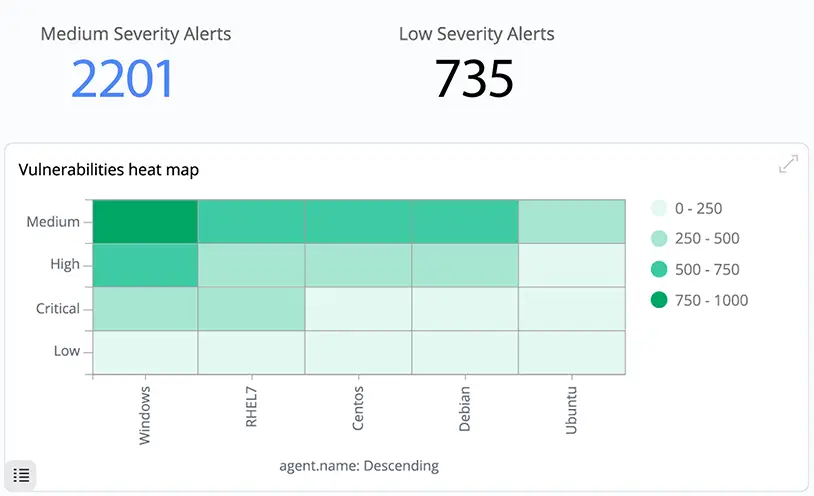
Protecting Your Business
In today’s connected world, cyber threats are becoming more advanced, targeted, and persistent than ever before. From ransomware and phishing to insider attacks, cloud vulnerabilities, and regulatory compliance risks, organizations face constant challenges that can disrupt operations, compromise sensitive data, and damage reputation. That’s why businesses need more than just security tools—they need a trusted partner with proven expertise, globally recognized certifications, and hands-on experience in real attack prevention and detection.

Our Cyber Security Services
Vulnerability Assessment & Penetration Testing (VAPT)
Comprehensive testing across web, mobile, cloud, and network environments.
Identify exploitable weaknesses before attackers can take advantage.
Detailed remediation plans to strengthen your security posture.
Threat Monitoring & Incident Response
24/7 Security Operations Center (SOC) with multi-tiered analysts (L1, L2, L3).
Real-time SIEM, log monitoring, IDS/IPS, and anomaly detection.
Rapid containment, investigation, and recovery from security incidents.
Data Protection & Business Continuity
Enterprise-grade encryption, secure backup, and disaster recovery planning.
Ensure critical assets remain protected, accessible, and recoverable.
Minimize downtime and guarantee uninterrupted business operations.
Compliance Consulting
Expertise in GDPR, HIPAA, PCI-DSS, ISO 27001, SOC 2, and local regulatory frameworks.
Map security controls to compliance requirements for audits and certifications.
Reduce compliance risk with proactive governance strategies.
Cloud Security
Security hardening across AWS, Azure, and GCP environments.
IAM, API, and instance-level protection with secure architecture design.
DevSecOps integration to embed security into the cloud lifecycle.
Endpoint & Network Security
Advanced endpoint protection (EDR, NAC) and deep traffic analysis.
Next-gen firewalls, intrusion prevention, and secure network segmentation.
Continuous monitoring to prevent lateral movement of threats.
Application Security
Secure coding practices, DevSecOps, and thorough code reviews.
Web and mobile application penetration testing.
Integration of security into CI/CD pipelines for ongoing protection.
Security Awareness & Testing
Employee training workshops and phishing simulations.
Red Team vs. Blue Team exercises to evaluate and strengthen defenses.
Build a culture of security awareness across your organization.
Why Choose Us?
In a world where cyber threats evolve daily, choosing the right security partner can make the difference between resilience and disruption. We combine deep expertise, cutting-edge technology, and proven frameworks to deliver security you can trust. From proactive monitoring to rapid response, our approach ensures your organization stays protected, compliant, and ahead of adversaries.
Threat Detection & Monitoring
Risk & Vulnerability Management
Response & Governance
Cloud & Modern Infrastructure
Intelligence & Insights
Secure you
Our Solutions
Cloud CLI

Private & Secure Email